How to: OpenERP 6.1, Ubuntu 10.04 LTS, nginx SSL Reverse Proxy
This article follows on (hopefully not unsurprisingly) from the basic 6.1 installation howto.
In this post I’ll describe one way of providing SSL encrypted access to your shiny new OpenERP 6.1 server running on Ubuntu 10.04 LTS.
This time I thought I’d use the nginx (pronounced like “Engine X”) webserver to act as a reverse proxy and do SSL termination for web, GTK client and WebDAV/CalDAV access. nginx is gaining in popularity and is now the second most popular web server in the world according to some figures. It has a reputation for being fast and lean – so it seemed like a good choice for a relatively simple job like this.
I’m indebted to xat for this post which provided the main configuration script for a reverse proxy on OpenERP 6.0. The changes I have made to xat’s original configuration are: different port number, some additional rewrite rules to support WebDAV and the new mobile interface, new location for static files.
NB: For the purposes of this how to, we’ll be using self-signed certificates. A discussion of the pros and cons of this choice is beyond the scope of this article.
Step 1. Install nginx
On your server install nginx by typing:
sudo apt-get install nginx
Next, we need to generate a SSL certificate and key.
Step 2. Create your cert and key
I create the files in a temporary directory then move them to their final resting place once they have been built (the first cd is just to make sure we are in our home directory to start with):
cd
mkdir temp
cd temp
Then we generate a new key, you will be asked to enter a passphrase and confirm:
openssl genrsa -des3 -out server.pkey 1024
We don’t really want to have to enter a passphrase every time the server starts up so we remove the passphrase by doing this:
openssl rsa -in server.pkey -out server.key
Next we need to create a signing request which will hold the data that will be visible in your final certificate:
openssl req -new -key server.key -out server.csr
This will generate a series of prompts like this: Enter the information as requested:
You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:
Email Address []:Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:The Client’s Company
And finally we self-sign our certificate.
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
We only need two of the files in the working directory, the key and the certificate. But before we can use them they need to have their ownership and access rights altered:
sudo chown root:www-data server.crt server.key
sudo chmod 640 server.crt server.key
And then we put them in a sensible place:
sudo mkdir /etc/ssl/nginx
sudo chown www-data:root /etc/ssl/nginx
sudo chmod 710 /etc/ssl/nginx
sudo mv server.crt server.key /etc/ssl/nginx/
Now the key and certificate are safely stored away, we can tell nginx where they are and what it should be doing…
Step 3. Create the nginx site configuration file
We create a new configuration file
sudo nano /etc/nginx/sites-available/openerp
with the following content:
Note: You will need to change all references to 10.0.0.26 in the following file to either the domain name or static IP address of your server. This was the IP address of the machine I built this test script on. It will not work unless changed to suit your own system!
upstream openerpweb { server 127.0.0.1:8069 weight=1 fail_timeout=300s; } server { listen 80; server_name 10.0.0.26; # Strict Transport Security add_header Strict-Transport-Security max-age=2592000; rewrite ^/mobile.*$ https://10.0.0.26/web_mobile/static/src/web_mobile.html permanent; rewrite ^/webdav(.*)$ https://10.0.0.26/webdav/$1 permanent; rewrite ^/.*$ https://10.0.0.26/web/webclient/home permanent; } server { # server port and name listen 443 default; server_name 10.0.0.26; # Specifies the maximum accepted body size of a client request, # as indicated by the request header Content-Length. client_max_body_size 200m; # ssl log files access_log /var/log/nginx/openerp-access.log; error_log /var/log/nginx/openerp-error.log; # ssl certificate files ssl on; ssl_certificate /etc/ssl/nginx/server.crt; ssl_certificate_key /etc/ssl/nginx/server.key; # add ssl specific settings keepalive_timeout 60; # limit ciphers ssl_ciphers HIGH:!ADH:!MD5; ssl_protocols SSLv3 TLSv1; ssl_prefer_server_ciphers on; # increase proxy buffer to handle some OpenERP web requests proxy_buffers 16 64k; proxy_buffer_size 128k; location / { proxy_pass http://openerpweb; # force timeouts if the backend dies proxy_next_upstream error timeout invalid_header http_500 http_502 http_503; # set headers proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forward-For $proxy_add_x_forwarded_for; # Let the OpenERP web service know that we're using HTTPS, otherwise # it will generate URL using http:// and not https:// proxy_set_header X-Forwarded-Proto https; # by default, do not forward anything proxy_redirect off; } # cache some static data in memory for 60mins. # under heavy load this should relieve stress on the OpenERP web interface a bit. location ~* /web/static/ { proxy_cache_valid 200 60m; proxy_buffering on; expires 864000; proxy_pass http://openerpweb; } }
UPDATE: 04/04/2012. I have added a line to the above file: client_max_body_size 200m; thanks to Praxi for reminding me about this. The default setting is just 1MB which will stop users from uploading any files larger than that, including databases!
And then we can enable the new site configuration by creating a symbolic link in the /etc/nginx/sites-enabled directory.
sudo ln -s /etc/nginx/sites-available/openerp /etc/nginx/sites-enabled/openerp
Step 4. Change the OpenERP server configuration file
The next step is to re-configure the OpenERP server so that non-encrypted services are not accessible from the outside world.
In /etc/openerp-server.conf the non-encrypted services will only listen on localhost, i.e. not from external connections so in effect only traffic from nginx will be accepted.
After opening the file for editing, just add 127.0.0.1 to the xmlrpc and netrpc interface lines as shown below.
sudo nano /etc/openerp-server.conf
xmlrpc_interface = 127.0.0.1
netrpc_interface = 127.0.0.1
That’s it. Everything is now configured.
Step 5. Try it out
Restart the services to load the new configurations
sudo service openerp-server restart
sudo service nginx restart
You should not be able to connect to the web client on port 8069 and the GTK client should not connect on either the NetRPC (8070) or XMLRPC (8069) services.
For web access you just need to visit https://your-ip-or-domain and in the GTK client you will need to use port 443 (https) and choose the XMLRPC (Secure) protocol.
The nginx configuration above will also redirect any incoming requests for port 80 to port 443 (https) and it also makes sensible redirects for the mobile and WebDAV/CalDAV services. (From what I can gather however WebDAV clients really don’t handle redirects so this bit is probably not that useful). I think the best bet for WebDAV/CalDAV is just to provide the correct URL in the first place.
For CalDAV access then, the URL to a calendar will be something like this:
https://your-ip-or-domain/webdav/DB_NAME/calendars/users/USERNAME/c/CALENDAR_NAME
There you have it. In OpenERP 6.1 this job actually proved to be a little simpler than the previous version largely due to the integrated web interface. There are also fewer configuration changes required in openerp-server.conf.
Finally, I really wanted to try and make use of the WSGI support in OpenERP 6.1 instead of the method above, but my efforts to get this to work from nginx or Apache have so far ended in failure 🙁 Obviously if anyone wants to provide a working config for that please feel free to add a comment and link.
How to install OpenERP 6.0 on Ubuntu 10.04 LTS Server (Part 2 – SSL)
This article follows on (hopefully not unsurprisingly) from part 1.
In this post I’ll describe our current way of providing SSL encrypted access to a shiny new OpenERP server running on Ubuntu 10.04 LTS Server.
We’re using the Apache webserver to act as a proxy and do SSL termination for web client access and for WebDAV/CalDAV access. The GTK client will also be running over an encrypted XMLRPC link directly to the OpenERP Server. Apache is the most widely used webserver in the world and there is oodles of documentation about it so I do not plan to go into any great detail about the configuration choices. One document that is worth pointing out however is the information about how to configure and administer Apache specifically under Debian/Ubuntu. The way Apache is packaged and set up is quite different from most other Linux distributions. A very useful document can be found here /usr/share/doc/apache2.2-common/README.Debian.gz on your server.
NB: For the purposes of this how to, we’ll be using self-signed certificates. A discussion of the pros and cons of this choice is beyond the scope of this article.
Step 1. Install Apache and required modules
On your server install apache2 by typing
sudo apt-get install apache2
Now we’ll tell apache that we want to use a few modules (mod_ssl, mod_proxy, mod_proxy_http, mod_headers and mod_rewrite [optional]) that are not enabled by default:
sudo a2enmod ssl proxy_http headers rewrite
Next, we need to generate a SSL certificate and key.
Step 2. Create your cert and key
I create the files in a temporary directory then move them to their final resting place once they have been built (the first cd is just to make sure we are in our home directory to start with):
cd
mkdir temp
cd temp
Then we generate a new key, you will be asked to enter a passphrase and confirm:
openssl genrsa -des3 -out server.pkey 1024
We don’t really want to have to enter a passphrase every time the server starts up so we remove the passphrase by doing this:
openssl rsa -in server.pkey -out server.key
Next we need to create a signing request which will hold the data that will be visible in your final certificate:
openssl req -new -key server.key -out server.csr
This will generate a series of prompts like this: Enter the information as requested:
You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:
Email Address []:Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:The Client’s Company
And finally we self-sign our certificate.
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
We only need two of the files in the working directory, the key and the certificate. But before we can use them they need to have their ownership and access rights altered:
sudo chown openerp:root server.crt server.key
sudo chmod 640 server.crt server.key
And then we put them in a sensible place:
sudo mkdir /etc/ssl/openerp
sudo chown openerp:root /etc/ssl/openerp
sudo chmod 710 /etc/ssl/openerp
sudo mv server.crt server.key /etc/ssl/openerp/
Now the key and certificate are safely stored away, we can tell Apache where they are:
Step 3. Create the Apache site configuration file
We create a new Virtual Host configuration file
sudo nano /etc/apache2/sites-available/openerp-ssl
with the following content:
SSLEngine on
SSLCertificateFile /etc/ssl/openerp/server.crt
SSLCertificateKeyFile /etc/ssl/openerp/server.keyProxyRequests Off
Order deny,allow
Allow from all
ProxyVia On
ProxyPass /webdav/ http://127.0.0.1:8069/webdav/
ProxyPassReverse /webdav/
Order Deny,Allow
Allow from all
Satisfy Any
ProxyPass / http://127.0.0.1:8080/
ProxyPassReverse /
RequestHeader set "X-Forwarded-Proto" "https"
# Fix IE problem (httpapache proxy dav error 408/409)
SetEnv proxy-nokeepalive 1
Note there are two Proxy configurations. One for /webdav/ and one for /. If you do not intend to use WebDAV or CalDAV then you can remove that section. But essentially, we are telling apache that WebDAV traffic needs to go to the XMLRPC port on the OpenERP server, and normal web traffic needs to go to the web client that is listening on port 8080. The order is also important. If / came before /webdav/ then it wouldn’t work.
And then we can enable the new site configuration.
sudo a2ensite openerp-ssl
Optionally, you can use mod_rewrite to redirect any normal (non-encrypted) web browser traffic to the SSL port (443).
To do this, add the following lines (outside of the /etc/apache2/sites-available/default
RewriteEngine on
RewriteCond %{SERVER_PORT} ^80$
RewriteRule ^(.*)$ https://%{SERVER_NAME}$1 [L,R]
Step 4. Change the OpenERP server and web-client configuration files
The next step is to re-configure the OpenERP server and Web client so that the non-encrypted services are not accessible from the outside world.
In /etc/openerp-server.conf the two non-encrypted services will only listen on localhost, i.e. not from external connections so in effect only traffic from Apache will be accepted. We also tell the XMLRPC-SSL service where to find the necessary key and certificate.
Make the following changes:
sudo nano /etc/openerp-server.conf
xmlrpc = True
xmlrpc_interface = 127.0.0.1
xmlrpc_port = 8069netrpc = True
netrpc_interface = 127.0.0.1
netrpc_port = 8070xmlrpcs = True
xmlrpcs_interface =
xmlrpcs_port = 8071
secure_pkey_file = /etc/ssl/openerp/server.key
secure_cert_file = /etc/ssl/openerp/server.crt
If you want to have WebDAV/CalDAV access add the following at the bottom of the config file.
[webdav]
enable = True
vdir = webdav
Then in the web client config file /etc/openerp-web.conf make the following changes so that it also only accepts traffic from localhost:
sudo nano /etc/openerp-web.conf
# Some server parameters that you may want to tweak
server.socket_host = “127.0.0.1”# Set to True if you are deploying your App behind a proxy
# e.g. Apache using mod_proxy
tools.proxy.on = True# If your proxy does not add the X-Forwarded-Host header, set
# the following to the *public* host url.
tools.proxy.base = ‘https://your-ip-or-domain’# Set to false to disable CSRF checks
tools.csrf.on = False
That’s it.
Step 5. Try it out
Restart the services to load the new configurations
sudo service openerp-server restart
sudo service openerp-web restart
sudo service apache2 restart
You should not be able to connect to the web client on port 8080 and the GTK client should not connect on either the NetRPC (8070) or XMLRPC (8069) services. For the web access you just need to visit https://your-ip-or-domain and in the GTK client you will need to use port 8071 and choose the XMLRPC (Secure) protocol.
For CalDAV access the URL to a calendar will be something like this:
https://your-ip-or-domain/webdav/DB_NAME/calendars/users/USERNAME/c/CALENDAR_NAME
I hope that is helpful and obviously we’d love to hear comments and suggestions for improvements.
How to install OpenERP 6.0 on Ubuntu 10.04 LTS Server (Part 1)
Update: 22/02/2012. OpenERP 6.1 was released today. I’ve written a howto for this new version here.
![]() Recently at work, we’ve been setting up several new instances of OpenERP for customers. Our server operating system of choice is Ubuntu 10.04 LTS.
Recently at work, we’ve been setting up several new instances of OpenERP for customers. Our server operating system of choice is Ubuntu 10.04 LTS.
Installing OpenERP isn’t really that hard, but having seen several other “How Tos” on-line describing various methods where none seemed to do the whole thing in what I consider to be “the right way”, I thought I’d explain how we do it. There are a few forum posts that I’ve come across where the advice is just plain wrong too, so do be careful.
As we tend to host OpenERP on servers that are connected to the big wide Internet, our objective is to end up with a system that is:
- A: Accessible only via encrypted (SSL) services from the GTK client, Web browser, WebDAV and CalDAV
- B: Readily upgradeable and customisable
One of my friends said to me recently, “surely it’s just sudo apt-get install openerp-server isn’t it?” Fair enough; this would actually work. But there are several problems I have with using a packaged implementation in this instance:
- Out-of-date. The latest packaged version I could see, in either the Ubuntu or Debian repositories, was 5.0.15. OpenERP is now at 6.0.3 and is a major upgrade from the 5.x series.
- Lack of control. Being a business application, with many configuration choices, it can be harder to tweak your way when the packager determined that one particular way was the “true path”.
- Upgrades and patches. Knowing how, where and why your OpenERP instance is installed the way it is, means you can decide when and how to update it and patch it, or add custom modifications.
So although the way I’m installing OpenERP below is manual, it gives us a much more fine-grained level of control. Without further ado then here is my way as it stands currently (“currently” because you can almost always improve things. HINT: suggestions for improvement gratefully accepted).
[Update 18/08/2011: I’ve updated this post for the new 6.0.3 release of OpenERP]
Step 1. Build your server
I install just the bare minimum from the install routine (you can install the openssh-server during the install procedure or install subsequently depending on your preference).
After the server has restarted for the first time I install the openssh-server package (so we can connect to it remotely) and denyhosts to add a degree of brute-force attack protection. There are other protection applications available: I’m not saying this one is the best, but it’s one that works and is easy to configure and manage. If you don’t already, it’s also worth looking at setting up key-based ssh access, rather than relying on passwords. This can also help to limit the potential of brute-force attacks. [NB: This isn’t a How To on securing your server…]
sudo apt-get install openssh-server denyhosts
Now make sure you are running all the latest patches by doing an update:
sudo apt-get update
sudo apt-get dist-upgrade
Although not always essential it’s probably a good idea to reboot your server now and make sure it all comes back up and you can still login via ssh.
Now we’re ready to start the OpenERP install.
Step 2. Create the OpenERP user that will own and run the application
sudo adduser --system --home=/opt/openerp --group openerp
This is a “system” user. It is there to own and run the application, it isn’t supposed to be a person type user with a login etc. In Ubuntu, a system user gets a UID below 1000, has no shell (well it’s actually /bin/false) and has logins disabled. Note that I’ve specified a “home” of /opt/openerp, this is where the OpenERP server, and optional web client, code will reside and is created automatically by the command above. The location of the server code is your choice of course, but be aware that some of the instructions and configuration files below may need to be altered if you decide to install to a different location.
Step 3. Install and configure the database server, PostgreSQL
sudo apt-get install postgresql
Then configure the OpenERP user on postgres:
First change to the postgres user so we have the necessary privileges to configure the database.
sudo su - postgres
Now create a new database user. This is so OpenERP has access rights to connect to PostgreSQL and to create and drop databases. Remember what your choice of password is here; you will need it later on:
createuser --createdb --username postgres --no-createrole --no-superuser --pwprompt openerp
Enter password for new role: ********
Enter it again: ********
[Update 18/08/2011: I have added the --no-superuser switch. There is no need for the openerp database user to have superuser privileges.]
Finally exit from the postgres user account:
exit
Step 4. Install the necessary Python libraries for the server
sudo apt-get install python python-psycopg2 python-reportlab \
python-egenix-mxdatetime python-tz python-pychart python-mako \
python-pydot python-lxml python-vobject python-yaml python-dateutil \
python-pychart python-webdav
And if you plan to use the Web client install the following:
sudo apt-get install python-cherrypy3 python-formencode python-pybabel \
python-simplejson python-pyparsing
Step 5. Install the OpenERP server, and optional web client, code
I tend to use wget for this sort of thing and I download the files to my home directory.
Make sure you get the latest version of the application files. At the time of writing this it’s 6.0.2 6.0.3; I got the download links from their download page.
wget http://www.openerp.com/download/stable/source/openerp-server-6.0.3.tar.gz
And if you want the web client:
wget http://www.openerp.com/download/stable/source/openerp-web-6.0.3.tar.gz
Now install the code where we need it: cd to the /opt/openerp/ directory and extract the tarball(s) there.
cd /opt/openerp
sudo tar xvf ~/openerp-server-6.0.3.tar.gz
sudo tar xvf ~/openerp-web-6.0.3.tar.gz
Next we need to change the ownership of all the the files to the openerp user and group.
sudo chown -R openerp: *
And finally, the way I have done this is to copy the server and web client directories to something with a simpler name so that the configuration files and boot scripts don’t need constant editing (I call them, rather unimaginatively, server and web). I started out using a symlink solution, but I found that when it comes to upgrading, it seems to make more sense to me to just keep a copy of the files in place and then overwrite them with the new code. This way you keep any custom or user-installed modules and reports etc. all in the right place.
sudo cp -a openerp-server-6.0.3 server
sudo cp -a openerp-web-6.0.3 web
As an example, should OpenERP 6.0.4 come out next, I can extract the tarballs into /opt/openerp/ as above. I can do any testing I need, then repeat the copy command (replacing 6.0.3 obviously) so that the modified files will overwrite as needed and any custom modules, report templates and such will be retained. Once satisfied the upgrade is stable, the older 6.0.3 directories can be removed if wanted.
That’s the OpenERP server and web client software installed. The last steps to a working system are to set up the two (server and web client) configuration files and associated init scripts so it all starts and stops automatically when the server boots and shuts down.
Step 6. Configuring the OpenERP application
The default configuration file for the server (in /opt/openerp/server/doc/) could really do with laying out a little better and a few more comments in my opinion. I’ve started to tidy up this config file a bit and here is a link to the one I’m using at the moment (with the obvious bits changed). You need to copy or paste the contents of this file into /etc/ and call the file openerp-server.conf. Then you should secure it by changing ownership and access as follows:
sudo chown openerp:root /etc/openerp-server.conf
sudo chmod 640 /etc/openerp-server.conf
The above commands make the file owned and writeable only by the openerp user and only readable by openerp and root.
To allow the OpenERP server to run initially, you should only need to change one line in this file. Toward to the top of the file change the line db_password = ******** to have the same password you used way back in step 3. Use your favourite text editor here. I tend to use nano, e.g. sudo nano /etc/openerp-server.conf
Once the config file is edited, you can start the server if you like just to check if it actually runs.
/opt/openerp/server/bin/openerp-server.py --config=/etc/openerp-server.conf
It won’t really work just yet as it isn’t running as the openerp user. It’s running as your normal user so it won’t be able to talk to the PostgreSQL database. Just type CTL+C to stop the server.
Step 7. Installing the boot script
For the final step we need to install a script which will be used to start-up and shut down the server automatically and also run the application as the correct user. Here’s a link to the one I’m using currently.
Similar to the config file, you need to either copy it or paste the contents of this script to a file in /etc/init.d/ and call it openerp-server. Once it is in the right place you will need to make it executable and owned by root:
sudo chmod 755 /etc/init.d/openerp-server
sudo chown root: /etc/init.d/openerp-server
In the config file there’s an entry for the server’s log file. We need to create that directory first so that the server has somewhere to log to and also we must make it writeable by the openerp user:
sudo mkdir /var/log/openerp
sudo chown openerp:root /var/log/openerp
Step 8. Testing the server
To start the OpenERP server type:
sudo /etc/init.d/openerp-server start
You should now be able to view the logfile and see that the server has started.
less /var/log/openerp/openerp-server.log
If there are any problems starting the server now you need to go back and check. There’s really no point ploughing on if the server doesn’t start…
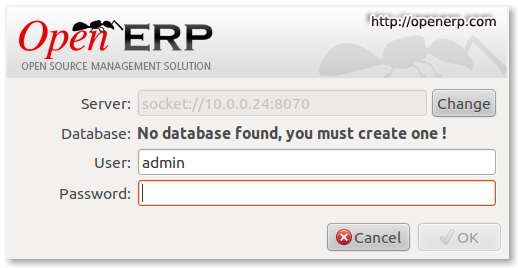
OpenERP - First Login
If you now start up the GTK client and point it at your new server you should see a message like this:
Which is a good thing. It means the server is accepting connections and you do not have a database configured yet. I will leave configuring and setting up OpenERP as an exercise for the reader. This is a how to for installing the server. Not a how to on using and configuring OpenERP itself…
What I do recommend you do at this point is to change the super admin password to something nice and strong. By default it is “admin” and with that a user can create, backup, restore and drop databases (in the GTK client, go to the file menu and choose the Databases -> Administrator Password option to change it). This password is written as plain text into the /etc/openerp-server.conf file. Hence why we restricted access to just openerp and root.
One rather strange thing I’ve just realised is that when you change the super admin password and save it, OpenERP completely re-writes the config file. It removes all comments and scatters the configuration entries randomly throughout the file. I’m not sure as of now if this is by design or not.
Now it’s time to make sure the server stops properly too:
sudo /etc/init.d/openerp-server stop
Check the logfile again to make sure it has stopped and/or look at your server’s process list.
Step 9. Automating OpenERP startup and shutdown
If everything above seems to be working OK, the final step is make the script start and stop automatically with the Ubuntu Server. To do this type:
sudo update-rc.d openerp-server defaults
You can now try rebooting you server if you like. OpenERP should be running by the time you log back in.
If you type ps aux | grep openerp you should see a line similar to this:
openerp 708 3.8 5.8 181716 29668 ? Sl 21:05 0:00 python /opt/openerp/server/bin/openerp-server.py -c /etc/openerp-server.conf
Which shows that the server is running. And of course you can check the logfile or use the GTK client too.
Step 10. Configure and automate the Web Client
Although it’s called the web client, it’s really another server-type application which [ahem] serves OpenERP to users via a web browser instead of the GTK desktop client.
If you want to use the web client too, it’s basically just a repeat of steps 6, 7, 8 and 9.
The default configuration file for the web client (can also be found in /opt/openerp/web/doc/openerp-web.cfg) is laid out more nicely than the server one and should work as is when both the server and web client are installed on the same machine as we are doing here. I have changed one line to turn on error logging and point the file at our /var/log/openerp/ directory. For our installation, the file should reside in /etc/, be called openerp-web.conf and have it’s owner and access rights set as with the server configuration file:
sudo chown openerp:root /etc/openerp-web.conf
sudo chmod 640 /etc/openerp-web.conf
Here is a web client boot script. This needs to go into /etc/init.d/, be called openerp-web and be owned by root and executable.
sudo chmod 755 /etc/init.d/openerp-web
sudo chown root: /etc/init.d/openerp-web
You should now be able to start the web server by entering the following command:
sudo /etc/init.d/openerp-web start
Check the web client is running by looking in the log file, looking at the process log and, of course, connecting to your OpenERP server with a web browser. The web client by default runs on port 8080 so the URL to use is something like this: http://my-ip-or-domain:8080
Make sure the web client stops properly:
sudo /etc/init.d/openerp-web stop
And then configure it to start and stop automatically.
sudo update-rc.d openerp-web defaults
You should now be able to reboot your server and have the OpenERP server and web client start and stop automatically.
I think that will do for this post. It’s long enough as it is!
I’ll do a part 2 in a little while where I’ll cover using apache, ssl and mod_proxy to provide encrypted access to all services.
[UPDATE: Part 2 is here]
Thunderbird 3 on a netbook?
I’ve been discussing the layout of the forthcoming TB3 release on their mailing list recently.
Since I installed it on my new Asus 1008HA on top of the Ubuntu Karmic Alpha build I’m having a bit of an issue with the [relatively] huge size of the header panel for messages. According to a quick measurement in the Gimp, the header is using 137px of vertical space. Netbooks typically have a 1024x600px resolution, some are even smaller. 137px represents almost 23% of the available vertical space.
Here’s a screenshot showing the typical layout I prefer clearly showing the space required by the header. Note that I also have the Calendar plugin Lightning installed too.
There used to be a “compact header” layout that took up much less space but allowed you to see more of the information if needed. But for reasons I do not understand that has been dropped from the current builds which seems a bit of a shame to me. The size of the header is making TB3 quite difficult to use on the increasingly popular and common ultra-portable devices. I am assuming this will be same if you are using another operating system too.
It was suggested that I try one of the other “views” or layouts that you can choose in TB and provide some screenshots too. Here you go then:
As you can see, the header impacts the available message body considerably in all layouts. One thing I realised though is these screenshots show a plain text email from a newsgroup reader. How about another common type of email then? HTML…
I find these images even more telling. Note how there is virtually no working space in the Classic View to determine if the mail is one you want to allow images to be loaded. I don’t think the Vertical view works at all and even the Wide View which is probably the most usable of the three seems to just draw your attention to the header and not to the message itself.
I also notice that there is a rather silly bit of wastage to do with the Calendar and Tasks buttons (underneath the search box). Why can’t they appear alongside the rest of the main toolbar? If you have multiple tabs accessible then I can see why we need the row to hold the tabs, But when there isn’t a tab open, is it really necessary? Whatever the case, I see no reason why the Lightning buttons need to have their own toolbar. That’s just waste and unintuitive. I’d expect those buttons to be with the others, not out on their own like that.
I will post a link to this blog page on the mozilla.dev.apps.thunderbird mailing list for all to see and hopefully comment.
Don’t get me wrong though. I really like Thunderbird. I have a strong preference to it over Evolution. Whenever I have tried Evolution I’ve found it difficult to use (in the sense it isn’t obvious), and it failed to work with our CalDAV calendars which was a known and long standing bug (I am not sure if this is still the case). It also didn’t feel as stable as TB, and considering I regularly use Alphas or nightly builds of Thunderbird and Lightning that is saying something. There is also a bug that has been open since 2004 with the title “Evolution is unusable in 800×600 or 1024×768”. It has seemingly received little attention since it was reported 5 years ago.
A recent post to the bug above pointed me to a blog post by Srini Ragavan discussing a new development going on for Evolution specifically to create a UI that is better suited to small resolution displays called Anjal.
Anjal looks to be a very interesting development and one I will be following closely. If Evolution gets to be as easy to use and as polished as I feel about Thunderbird, then I might well end up giving it a try again.









