Finding VirtualBox IP addresses
I have been running some server instances in VirtualBox recently and as I move between networks it is a pain to have to log in and get the IP address from ipconfig before being able to access the test web sites I have running in them. I also prefer to SSH to them rather than use the VirtualBox instance (it gives better character screen size, although I could reconfigure things; I also tab my terminals).
Anyway, in order to make things easier I put together two scripts, one that handles getting the IP address of the Virtualbox instance, and the other that handles connecting via SSH just by telling it the instance name. In order to do this you need to install the VirtualBox Guest Additions. This package is generally used in connection with video drivers for GUI based guests, but it also has some extensions that present extra information about the guest to the host machine.
Installing on Ubuntu is quite easy. My setup is using Ubuntu 12.10 on the desktop (host) and Ubuntu 12.04 LTS on the server (guest). To start with there is a package with the Guest Additions ISO in, so start by installing it with:
sudo aptitude install virtualbox-guest-additions-iso
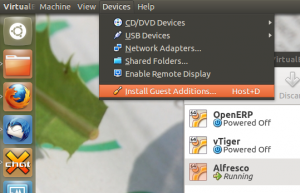
Next you need to mount the ISO in the guest OS. To do this choose the Install Guest Additions option from the Devices menu. Since this is a CLI server OS it won’t automatically mount the ISO, so you will have to do this manually with:
sudo mount /dev/cdrom /media/cdrom
Once you have done this you need to install dkms and then run the install script with:
sudo aptitude install dkms
sudo /media/cdrom/VBoxLinuxAdditions.run
It will complain about not having found X to install the graphics drivers, but this isn’t a problem.
Once you have done this you can use the command:
VBoxManage guestproperty enumerate
where <vname> is the name of your guest. This will list out all of the available information that can now be accessed.
Using this command in a little bit of bash I created the two scripts. Firstly to get the IP address of a named guest:
#! /bin/bash
VIP=`VBoxManage guestproperty get $1 "/VirtualBox/GuestInfo/Net/0/V4/IP" | awk '{print $2}'`
echo $VIP
Secondly, to SSH to a named guest:
#! /bin/bash
VIP=`VBoxManage guestproperty get $1 "/VirtualBox/GuestInfo/Net/0/V4/IP" | awk '{print $2}'`
ssh-keygen -f "/home/paul/.ssh/known_hosts" -R $VIP
ssh $VIP
This second one is a little more involved because it first deletes the entry from the known_host file (remember to change the location). I’ve done this to stop an error coming up if the IP address has already been used, which isn’t uncommon with DHCP leases (you often get the same one, but not always!). You will have to confirm the authenticity of the host each time you connect, but since this is scripted and the IP has been automatically obtained locally to the machine this shouldn’t present a security risk.
Each of these scripts takes the guest name as a parameter, eg:
vbip Alfresco
or
vssh Alfresco
Lastly, to make these new scripts easy to use I created a .bash_aliases file in my home directory with the following:
## custom aliases
alias vssh='~/scripts/vssh'
alias vbip='~/scripts/vbip'
You will need to adjust for whever you have put these scripts, I tend to have a scripts directory in my home directory for this purpose.
How to install OpenERP 7.0 on Ubuntu 12.04 LTS
Introduction
Welcome to the latest of our very popular OpenERP installation “How Tos”.
The new release of OpenERP 7.0 is a major upgrade and a new Long Term Support release; the 7.0 Release Notes extend to over 90 pages! The most noticeable change is a complete re-write of the User Interface that features a much more modern look and feel.
OpenERP 7.0 is not only better looking and easier to use, it also brings many improvements to the existing feature-set and adds a number of brand new features which extend the scope of the business needs covered by OpenERP. Integration of social network capabilities, integration with Google Docs and LinkedIn, new Contract Management, new Event Management, new Point of Sale, new Address Book, new Fleet Management,… are only some of the many enhancements in OpenERP 7.0.
The How To
Following that introduction, I bet you can’t wait to get your hands dirty…
Just one thing before we start: You can simply download a “.deb†package of OpenERP and install that on Ubuntu. Unfortunately that approach doesn’t provide us (Libertus Solutions) with enough fine-grained control over where things get installed, and it restricts our flexibility to modify & customise, hence I prefer to do it a slightly more manual way (this install process below should only take about 10-15 minutes once the host machine has been built).
So without further ado here we go:
Step 1. Build your server
I install just the bare minimum from the install routine (you may want to install the openssh-server during the install procedure or install subsequently depending on your needs).
After the server has restarted for the first time I install the openssh-server package (so we can connect to it remotely) and denyhosts to add a degree of brute-force attack protection. There are other protection applications available: I’m not saying this one is the best, but it’s one that works and is easy to configure and manage. If you don’t already, it’s also worth looking at setting up key-based ssh access, rather than relying on passwords. This can also help to limit the potential of brute-force attacks. [NB: This isn’t a How To on securing your server…]
sudo apt-get install openssh-server denyhosts
Now make sure your server has all the latest versions & patches by doing an update:
sudo apt-get update
sudo apt-get dist-upgrade
Although not always essential it’s probably a good idea to reboot your server now and make sure it all comes back up and you can login via ssh.
Now we’re ready to start the OpenERP install.
Step 2. Create the OpenERP user that will own and run the application
sudo adduser --system --home=/opt/openerp --group openerp
This is a “system†user. It is there to own and run the application, it isn’t supposed to be a person type user with a login etc. In Ubuntu, a system user gets a UID below 1000, has no shell (it’s actually /bin/false) and has logins disabled. Note that I’ve specified a “home†of /opt/openerp, this is where the OpenERP server code will reside and is created automatically by the command above. The location of the server code is your choice of course, but be aware that some of the instructions and configuration files below may need to be altered if you decide to install to a different location.
[Note: If you want to run multiple versions of OpenERP on the same server, the way I do it is to create multiple users with the correct version number as part of the name, e.g. openerp70, openerp61 etc. If you also use this when creating the Postgres users too, you can have full separation of systems on the same server. I also use similarly named home directories, e.g. /opt/openerp70, /opt/openerp61 and config and start-up/shutdown files. You will also need to configure different ports for each instance or else only the first will start.]
A question I have been asked a few times is how to run the OpenERP server as the openerp system user from the command line if it has no shell. This can be done quite easily:
sudo su - openerp -s /bin/bash
This will su your current terminal login to the openerp user (the “-” between su and openerp is correct) and use the shell /bin/bash. When this command is run you will be in openerp’s home directory: /opt/openerp.
When you have done what you need you can leave the openerp user’s shell by typing exit.
Step 3. Install and configure the database server, PostgreSQL
sudo apt-get install postgresql
Then configure the OpenERP user on postgres:
First change to the postgres user so we have the necessary privileges to configure the database.
sudo su - postgres
Now create a new database user. This is so OpenERP has access rights to connect to PostgreSQL and to create and drop databases. Remember what your choice of password is here; you will need it later on:
createuser --createdb --username postgres --no-createrole --no-superuser --pwprompt openerp
Enter password for new role: ********
Enter it again: ********
Finally exit from the postgres user account:
exit
Step 4. Install the necessary Python libraries for the server
sudo apt-get install python-dateutil python-docutils python-feedparser python-gdata \
python-jinja2 python-ldap python-libxslt1 python-lxml python-mako python-mock python-openid \
python-psycopg2 python-psutil python-pybabel python-pychart python-pydot python-pyparsing \
python-reportlab python-simplejson python-tz python-unittest2 python-vatnumber python-vobject \
python-webdav python-werkzeug python-xlwt python-yaml python-zsi
With that done, all the dependencies for installing OpenERP 7.0 are now satisfied (note that there are some new packages required since 6.1).
Step 5. Install the OpenERP server
I tend to use wget for this sort of thing and I download the files to my home directory.
Make sure you get the latest version of the application: at the time of writing this it’s 7.0. I got the download links from their download pages (note there are also deb, rpm and exe builds in this area too). There isn’t a static 7.0 release tarball as such anymore, but there is a nightly build of the 7.0 source tree which should be just as good and will contain patches as and when things get fixed. The link below is to the source tarball for the 7.0 branch.
Note: As an alternative method of getting the code onto your server, Jerome added a very useful comment showing how to get it straight from launchpad. Thanks!
wget http://nightly.openerp.com/7.0/nightly/src/openerp-7.0-latest.tar.gz
Now install the code where we need it: cd to the /opt/openerp/ directory and extract the tarball there.
cd /opt/openerp
sudo tar xvf ~/openerp-7.0-latest.tar.gz
Next we need to change the ownership of all the the files to the OpenERP user and group we created earlier.
sudo chown -R openerp: *
And finally, the way I have done this is to copy the server directory to something with a simpler name so that the configuration files and boot scripts don’t need constant editing (I called it, rather unimaginatively, server). I started out using a symlink solution, but I found that when it comes to upgrading, it seems to make more sense to me to just keep a copy of the files in place and then overwrite them with the new code. This way you keep any custom or user-installed modules and reports etc. all in the right place.
sudo cp -a openerp-7.0 server
As an example, should OpenERP 7.0.1 come out soon, I can extract the tarballs into /opt/openerp/ as above. I can do any testing I need, then repeat the copy command so that the modified files will overwrite as needed and any custom modules, report templates and such will be retained. Once satisfied the upgrade is stable, the older 7.0 directories can be removed if wanted.
That’s the OpenERP server software installed. The last steps to a working system is to set up the configuration file and associated boot script so OpenERP starts and stops automatically when the server itself stops and starts.
Step 6. Configuring the OpenERP application
The default configuration file for the server (in /opt/openerp/server/install/) is actually very minimal and will, with only one small change work fine so we’ll simply copy that file to where we need it and change it’s ownership and permissions:
sudo cp /opt/openerp/server/install/openerp-server.conf /etc/
sudo chown openerp: /etc/openerp-server.conf
sudo chmod 640 /etc/openerp-server.conf
The above commands make the file owned and writeable only by the openerp user and group and only readable by openerp and root.
To allow the OpenERP server to run initially, you should only need to change one line in this file. Toward to the top of the file change the line db_password = False to the same password you used back in step 3. Use your favourite text editor here. I tend to use nano, e.g.
sudo nano /etc/openerp-server.conf
One other line we might as well add to the configuration file now, is to tell OpenERP where to write its log file. To complement my suggested location below add the following line to the openerp-server.conf file:
logfile = /var/log/openerp/openerp-server.log
Once the configuration file is edited and saved, you can start the server just to check if it actually runs.
sudo su - openerp -s /bin/bash
/opt/openerp/server/openerp-server
If you end up with a few lines eventually saying OpenERP is running and waiting for connections then you are all set.
On my system I noticed the following warning:
2012-12-19 11:53:51,613 6586 WARNING ? openerp.addons.google_docs.google_docs: Please install latest gdata-python-client from http://code.google.com/p/gdata-python-client/downloads/listThe Ubuntu 12.04 packaged version of the python gdata client library is not quite recent enough, so to install a more up-to-date version I did the following (exit from the openerp user’s shell if you are still in it first):
sudo apt-get install python-pip
sudo pip install gdata --upgradeGoing back and repeating the commands to start the server resulted in no further warnings
sudo su - openerp -s /bin/bash
/opt/openerp/server/openerp-server
If there are errors, you’ll need to go back and find out where the problem is.
Otherwise simply enter CTL+C to stop the server and then exit to leave the openerp user account and go back to your own shell.
Step 7. Installing the boot script
For the final step we need to install a script which will be used to start-up and shut down the server automatically and also run the application as the correct user. There is a script you can use in /opt/openerp/server/install/openerp-server.init but this will need a few small modifications to work with the system installed the way I have described above. Here’s a link to the one I’ve already modified for 7.0.
Similar to the configuration file, you need to either copy it or paste the contents of this script to a file in /etc/init.d/ and call it openerp-server. Once it is in the right place you will need to make it executable and owned by root:
sudo chmod 755 /etc/init.d/openerp-server
sudo chown root: /etc/init.d/openerp-server
In the configuration file there’s an entry for the server’s log file. We need to create that directory first so that the server has somewhere to log to and also we must make it writeable by the openerp user:
sudo mkdir /var/log/openerp
sudo chown openerp:root /var/log/openerp
Step 8. Testing the server
To start the OpenERP server type:
sudo /etc/init.d/openerp-server start
You should now be able to view the logfile and see that the server has started.
less /var/log/openerp/openerp-server.log
If there are any problems starting the server you need to go back and check. There’s really no point ploughing on if the server doesn’t start…
If the log file looks OK, now point your web browser at the domain or IP address of your OpenERP server (or localhost if you are on the same machine) and use port 8069. The url will look something like this:
http://IP_or_domain.com:8069
What you should see is a screen like this one (it is the Database Management Screen because you have no OpenERP databases yet):
What I do recommend you do at this point is to change the super admin password to something nice and strong (Click the “Password” menu). By default this password is just “admin” and knowing that, a user can create, backup, restore and drop databases! This password is stored in plain text in the /etc/openerp-server.conf file; hence why we restricted access to just openerp and root. When you change and save the new password the /etc/openerp-server.conf file will be re-written and will have a lot more options in it.
Now it’s time to make sure the server stops properly too:
sudo /etc/init.d/openerp-server stop
Check the logfile again to make sure it has stopped and/or look at your server’s process list.
Step 9. Automating OpenERP startup and shutdown
If everything above seems to be working OK, the final step is make the script start and stop automatically with the Ubuntu Server. To do this type:
sudo update-rc.d openerp-server defaults
You can now try rebooting you server if you like. OpenERP should be running by the time you log back in.
If you type ps aux | grep openerp you should see a line similar to this:
openerp 1491 0.1 10.6 207132 53596 ? Sl 22:23 0:02 python /opt/openerp/server/openerp-server -c /etc/openerp-server.conf
Which shows that the server is running. And of course you can check the logfile or visit the server from your web browser too.
That’s it! Next I would suggest you create a new database filling in the fields as desired. Once the database is initialised, you will be directed straight to the new main configuration screen which gives you a fell for the new User Interface in OpenERP 7 and shows you how easy it is to set up a basic system.
Actions from Ubuntu UDS-R
This week was the Ubuntu Developer Summit in Copenhagen, this is kind of an internal series of workshops, but as Ubuntu is an open project it isn’t a closed doors event. Anyone can attend in person, some people are sponsored by Canonical to attend. Others (like me this time) can follow along remotely via live video and audio streams and IRC talk back to the workshop rooms. The full schedule was here, and the proceedings of each session are recorded on an Etherpad page. I wrote some scripts to download all the text of these pages and scoop out the action items and you can find that over here. These will all get processed and end up on status.ubuntu.com as pretty burndown charts for ongoing tracking, but this is a quick and dirty list of all of them.
Time for an Upgrade
The Ubuntu UK Local Team allocation of CDs arrived yesterday and as usual these are available for free to anyone who wants one in the UK. Just send me an SAE following the procedure here and please please try to put enough postage on it, I get bored of walking to the post office to pay the fine.
If you want several of them to hand out at an event then please get in touch and we can sort that out.
As usual there is one special CD that gets upgraded each release, the one my chickens peck at! They were using Ubuntu Server 12.04 LTS before, but today I upgraded them to Ubuntu Server 12.10 the Quantal Qetzal. I think they were pleased at the bird themed code name and they have been getting quite familiar with the command line over the last few months. I tested the retired 12.04 CD and it still works great in a computer after washing the muck off it.

Would you put that in your chicken run?

It might have Long Term Support, but would you put it in your laptop?
OpenERP and Ubuntu Unity Desktop Integration
Ubuntu has been in the news quite a lot recently with the release of version 12.10 including the Amazon shopping lens and next week some game shop thing called Steam is going to be announced. It isn’t all toys and shopping though, some of the new features make a heap of sense for serious business applications too. One really interesting area for me is the webapp integration, this is an extension for Firefox and Chromium that allows stuff running in the web browser to integrate with the Unity desktop in a variety of ways, making the distinction between a web application and a desktop application a bit more blurry – which is a good thing. There is built in integration for an assortment of popular consumer websites like youtube, twitter, facebook etc. but it isn’t limited to these single domain software as a service sites. Any web site or web application can test for the presence of the extension then export it’s menu items, do notifications and other actions.
OpenERP is probably my favourite web application to work on, and this is a typical application you might install to help manage a business, it is a modular framework that covers accountancy, logistics, sales process, project management, manufacturing, HR etc. The web server is largely python based, but as it happens this integration just uses javascript. After you install the module and visit your OpenERP server you should be prompted to allow integration, if you accept this you will get a notification (bubble in the top right of the screen) to say it is activated and from then you can use the alt key to bring up the HUD and type anything you might find in an OpenERP menu somewhere, such as “Invoice”. You don’t have to type all of the word, it will search as you type.
You can grab the code from here and the module as a standard module zip file from here. I am thinking of adding some more features, possibly messaging menu integration and notifications. I might do a separate theme module that is mostly CSS and cosmetically adjusts the user interface to match the unity desktop. Right now most of our customers running OpenERP use it on an Ubuntu server, but use a mixture of Windows and Mac on the desktop, what I want to show with this kind of integration (this is just the start) is that Ubuntu can simply be a better platform for business than other operating systems, especially as things move away from dedicated client applications to web based interfaces.
The Quantal Quetzal takes flight
 Â A week today on the 18th October is the release date of Ubuntu 12.10 the Quantal Quetzal. This release was pitched to be all about quality and from my testing I think the quality has improved quite a lot. If you were thinking of trying Ubuntu with the Unity interface then 12.10 is the release to go for, a lot of niggles have been unniggled and sharp edges smoothed over.
 A week today on the 18th October is the release date of Ubuntu 12.10 the Quantal Quetzal. This release was pitched to be all about quality and from my testing I think the quality has improved quite a lot. If you were thinking of trying Ubuntu with the Unity interface then 12.10 is the release to go for, a lot of niggles have been unniggled and sharp edges smoothed over.
As is traditional with Ubuntu releases there will be a party in London where users, enthusiasts and the Canonical release team get together to consume some adult beverages and generally have a fun evening. This release is no exception to the tradition and you are most welcome to join us at the George Inn from about 7ish (or whenever you can). There is an optional sign up sheet with more details, anyone on the list will probably have a name badge waiting for them (this is based on feedback from previous events).
If you want to get your hands on an official Ubuntu 12.10 DVD we are now taking pre-orders for the UK local team allocation just send in an SAE they will probably arrive around the end of the month or early November.